
LastPass is warning clients of a phishing marketing campaign sending emails with an entry request to the password vault as a part of a legacy inheritance course of.
The exercise began in mid-October, and the domains and infrastructure used level to a financially motivated menace group known as CryptoChameleon (UNC5356).
CryptoChamemelon employs a phishing package specializing in cryptocurrency theft, focusing on a number of wallets together with Binance, Coinbase, Kraken, and Gemini, utilizing faux Okta, Gmail, iCloud, and Outlook sign-in pages.
LastPass customers have been focused by the identical group once more in April 2024however the most recent marketing campaign seems to be extra in depth and in addition enhanced, now focusing on passkeys too.
The phishing emails despatched to LastPass customers declare {that a} member of the family requested entry to their LastPass vault by importing a loss of life certificates.
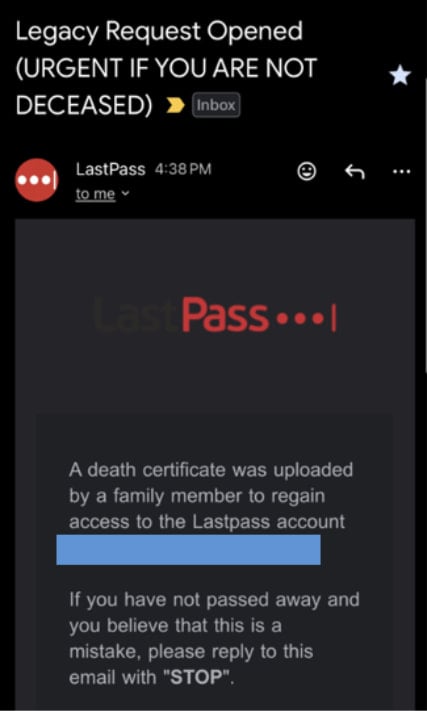
Supply: LastPass
LastPass’s inheritance course of is an emergency entry function that permits people designated by account holders to request entry to their vault in case of loss of life or incapacity.
When such a request is opened, the account holder receives an e mail, and after a ready interval expires, entry is routinely granted to the contact.
The fabricated legacy request consists of an agent ID quantity for added legitimacy, prompting the recipient to take motion and cancel it if they don’t seem to be deceased by clicking a hyperlink.
Nonetheless, the hyperlink redirects them to a fraudulent web page on lastpassrecovery(.)com that includes a login type the place the sufferer can enter their grasp password.
LastPass says that in some instances the menace actor known as victims posing as LastPass employees and directed them to enter their credentials on the phishing website.
The corporate says that one key factor within the CryptoChameleon assault focusing on its customers is using passkey-focused phishing domains equivalent to mypasskey(.)data and passkeysetup(.)comwhich point out makes an attempt to steal customers’ passkeys.
Passkeys are a passwordless authentication normal based mostly on the FIDO2 / WebAuthn protocols, utilizing assymmetric cryptography as an alternative of memorized passwords.
Fashionable password managers like LastPass, 1Password, Dashlane, and Bitwarden now retailer and sync passkeys throughout units, and menace actors have began to focus on them immediately.
In 2022, LastPass suffered a significant information breach the place attackers stole encrypted vault backups. The incident was linked to focused assaults that adopted, leading to losses of roughly $4.4 million in cryptocurrency.


