
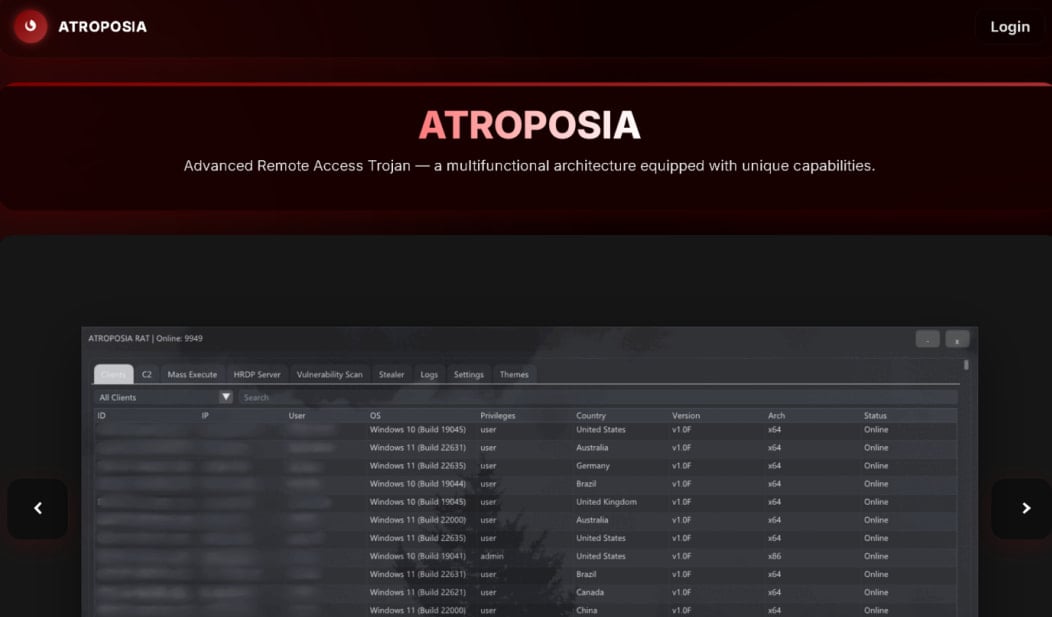
A brand new malware-as-a-service (MaaS) platform named Atroposia offers cybercriminals a distant entry trojan that mixes capabilities for persistent entry, evasion, knowledge theft, and native vulnerability scanning.
The malware is out there for a $200 month-to-month subscription that unlocks superior options resembling hidden distant desktop, file system management, knowledge exfiltration, clipboard theft, credential theft, cryptocurrency pockets theft, and DNS hijacking.
Atroposia was found by researchers at knowledge safety firm Varonis, who warned that it’s the newest instance of an easy-to-use, reasonably priced “plug and play” toolkit, alongside SpamGPT and MatrixPDF.
Supply: Hero
Atroposia overview
Atroposia is a modular RAT that communicates with its command-and-control (C2) infrastructure over encrypted channels and may bypass the Person Account Management (UAC) safety to extend privileges privilege on Home windows programs.
In line with the researchers, it could keep persistent, stealthy entry on contaminated hosts, and its primary capabilities embrace:
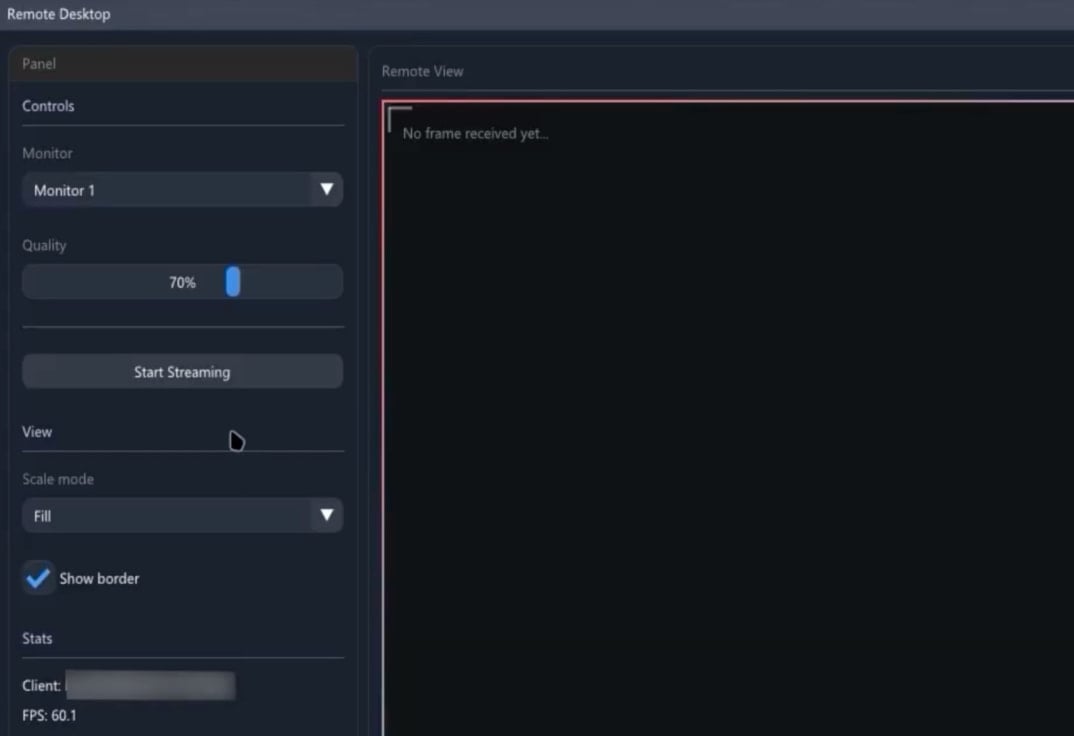
- HRDP Join module that spawns a covert desktop session within the background, permitting an attacker to open apps, view paperwork and electronic mail, and work together with the person’s session with none seen indication. Varonis says normal remote-access monitoring can fail to detect it.
Supply: Hero
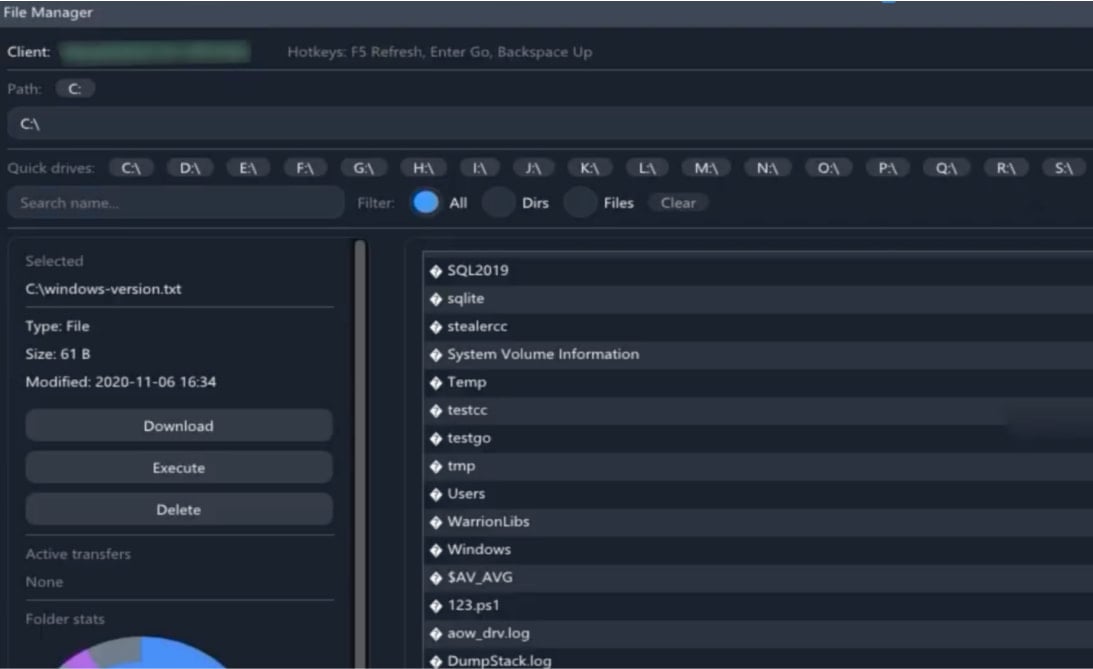
- Explorer-style file supervisor that enables distant file looking copying, deleting, and execution capabilities. A grabber element appears to be like for particular information, filtering them primarily based on extension or a key phrase, compresses the info into password-protected ZIP archives, and exfiltrates it utilizing in-memory strategies to reduce traces.
Supply: Hero
- Stealer module targets saved logins, crypto wallets, and chat information, whereas a clipboard supervisor captures every part copied in actual time (passwords, API keys, pockets addresses) and presents a historical past to the attacker.
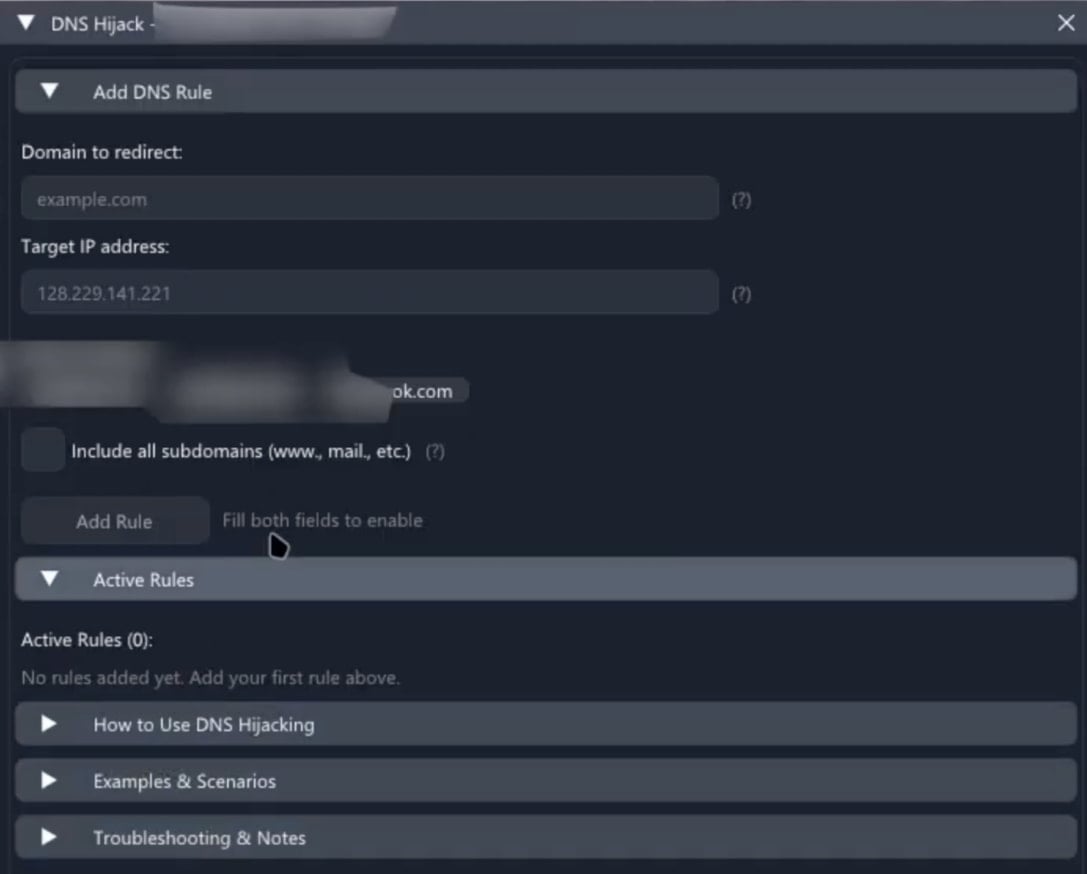
- Host-level DNS hijack module that maps domains to attacker IPs so the sufferer is silently routed to rogue servers, enabling phishing, MITM, pretend updates, advert or malware injection, and DNS-based exfiltration.
Supply: Hero
- Constructed-in native vulnerability scanner that audits lacking patches, unsafe settings, and susceptible software program, returning a rating that enables attackers to prioritize exploits, demonstrating the RAT’s modular, plugin-based workflow.
The researchers say that the vulnerability examine “is harmful in company environments as a result of the malware would possibly discover an outdated VPN shopper or an unpatched privilege escalation bug.” This may be simply used to achieve deeper entry.
In line with a report from Varonis, the module checks for lacking patches, insecure settings, and outdated software program variations. The perform can also be used to seek out close by programs that may be exploited.
The emergence of Atroposia provides yet one more MaaS possibility for cybercriminals, reducing the technical barrier and enabling low-skilled menace actors to execute efficient campaigns.
To mitigate the chance, customers are suggested to obtain software program solely from official websites and respected sources, keep away from pirated software program and torrents, skip promoted search outcomes, and by no means execute instructions they discover on-line that they don’t perceive.


